Operational technology vulnerabilities increased by 46%, Skybox Security research reveals
New threat intelligence research finds critical infrastructure at heightened risk
News summary
- New vulnerabilities exploited in the wild grew by 30% in H1 2021
- Ransomware grew by nearly 20%
- Cryptomining malware more than doubled
- Cumulative number of known vulnerabilities grew 3x in 10 years
- Download the full report
SAN JOSE, Calif., Sept. 14, 2021 /PRNewswire/ -- Skybox Security, a global leader in security posture management, today released its annual Mid-Year Vulnerability and Threat Trends Report, offering new threat intelligence research on the frequency and scope of global malicious activity. The Skybox Research Lab analysts found that new vulnerabilities in operational technology (OT) devices were up 46% in the first half of 2021, putting vital critical infrastructure at risk.
"Critical infrastructure is the backbone of global enterprises and governments. Operational technology enables revenue creation and business continuity. Yet, despite the criticality, the cybersecurity measures in place are still weak or nonexistent," said Gidi Cohen, CEO and founder, Skybox Security. "Experts warned for years that vital infrastructure is a sitting duck and that it was only a matter of time before they came under widespread assault. Now, those predictions have come true."
To make matters worse, it can be difficult or impossible to identify and remediate OT vulnerabilities through scanning and patching. Nearly all major vendors of OT equipment reported increases in vulnerabilities, especially Siemens. Threat actors are taking advantage of these OT weaknesses in ways that don't just imperil individual companies but also threaten public safety and the global economy.
Skybox Security threat intelligence analyzes exploits in the wild to prioritize vulnerabilities that need remediation. Key findings presented in this mid-year update include:
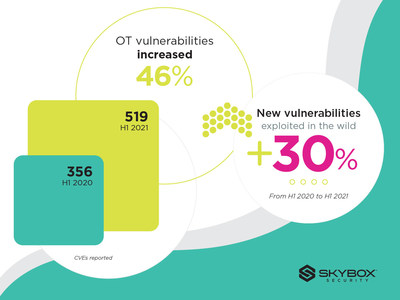
* OT vulnerabilities up 46%
New vulnerabilities in OT devices were up nearly 46% versus H1 2020. These vulnerabilities pose a growing threat to critical infrastructure and other vital systems. Cybercriminals know how indispensable OT assets and their control systems are, and companies will pay hefty ransoms to avoid disruptions and shutdowns.
* Exploits in the wild increased by 30%
The number of new vulnerabilities exploited in the wild grew 30% in H1 2021 compared to the same period last year. Interestingly, a growing percentage of these exploits (13% in H1 2021 versus 8% in 2020) are specifically targeting vulnerabilities rated as "medium-severity" on the CVSS scale. Thus, as new security weaknesses emerge, threat actors are moving quickly to take advantage of them.
* Network device vulnerabilities grew by nearly 20%
The number of network devices such as routers, switches, firewalls, and their operating systems, rose nearly 20% in H1 2021. Like OT, these devices are critically important parts of the infrastructure, yet their security flaws are often invisible because they are difficult or impossible to effectively scan. Scanning can impact performance or even shut down systems and is further complicated by the need for special passwords and access privileges.
* Ransomware up 20%
Ransomware increased by 20% versus the first half of 2020. Interestingly, new malware overwhelmingly exploited more recent vulnerabilities (vulnerabilities reported in the last 3 years). This clearly indicates that malware creators have new vulnerabilities on their radar and actively develop novel malware to exploit the latest weaknesses.
* Cryptojacking more than doubled
Cryptojacking malware, which hijacks computer systems for cryptocurrency mining, more than doubled in comparison to the same period last year. Cryptojacking is just one example of how dynamic an industry malware has become, quickly adapting its offerings and business models to serve emerging markets. In some cases, malware-as-a-service providers lease botnets composed of already-infected machines to cryptominers.
* Cumulative number of vulnerabilities grows 3x in 10 years
This cumulative number of vulnerabilities is concerning. The vast majority of vulnerabilities aren't new, and the older they are, the more time threat actors have had to find and exploit. Old vulnerabilities lurk for years in networks, only to become exposed later, offering rich targets for attackers. Some of the most exploited vulnerabilities are 4 years old or more.
"The sheer volume of accumulated security debt — hundreds of thousands or even millions of vulnerabilities — means that security teams can't possibly isolate and patch all of them. Malware evolves like viruses, with new variants springing up opportunistically in response to changing environments," said Stav Kaufman, lead analyst, Skybox Research Lab. "As a result, enterprises need precise, exposure-based solutions that cut through the noise, pinpoint the real security threats and enable practical, cost-effective remediation."
For more threat intelligence analysis, download the full report.
Methodology
Skybox Research Lab analysts continuously monitor dozens of security sources, tracking and analyzing hundreds of thousands of vulnerabilities on over ten thousand products, along with the latest data on available exploits and malware taking advantage of these vulnerabilities. The analysts identify the vulnerabilities most likely to impact our customers' unique networks and assets. This threat intelligence powers Skybox's vulnerability and threat management solution and enables our customers to discover, prioritize and remediate risks.
About Skybox Security
Over 500 of the largest and most security-conscious enterprises in the world rely on Skybox for the insights and assurance required to stay ahead of dynamically changing attack surfaces. At Skybox, we don't just serve up data and information. We provide the intelligence and context to make informed decisions, taking the guesswork out of securely enabling enterprises at scale and speed. Our unified security posture management platform delivers complete visibility, analytics, and automation to quickly map, prioritize, and remediate vulnerabilities across your organization. The vendor-agnostic platform intelligently optimizes security policies, actions, and change processes across all corporate and cloud environments. With Skybox, security teams can focus on the most strategic business initiatives while ensuring that enterprises remain protected.
We are Skybox. Secure more, limit less. https://www.skyboxsecurity.com/
Media & analyst contact
Ashley Nakano
Corporate Communications
skyboxglobal@allisonpr.com
© 2021 Skybox Security, Inc. All rights reserved. Skybox Security and the Skybox Security logo are either registered trademarks or trademarks of Skybox Security, Inc., in the United States and/or other countries. All other trademarks are the property of their respective owners. Product specifications subject to change at any time without prior notice.
Photo - https://mma.prnewswire.com/media/1624858/Skybox_Security_midyear_report.jpg
Logo - https://mma.prnewswire.com/media/1011662/Skybox_Security_logo.jpg
Like this content? Sign up for our daily newsletter to get latest updates.
0
Subscribe to:
Post Comments (Atom)
both, mystorymag














 IndianWeb2.com is an independent digital media platform for business, entrepreneurship, science, technology, startups, gadgets and climate change news & reviews.
IndianWeb2.com is an independent digital media platform for business, entrepreneurship, science, technology, startups, gadgets and climate change news & reviews.



